Static Code Analysis to Accelerate Standards Compliance & Quality Insights
QA-MISRA SUPPORTED CODING STANDARDS
EXPLORE QA-MISRA
Hover over the options to learn more.

Coding Standards Compliance
Check your C/C++ source code for compliance with internationally recognised coding guidelines and rules.

Metrics & Visualisations
Metrics & Visualisations
QA-MISRA provides quality insights through metrics and visualisations to understand your code better.

Why invest in QA-MISRA?
Industry leaders use QA-MISRA to accelerate analysis times and standards compliance, and increase confidence by reducing errors in syntactic coding rules and improving source code quality.
HOW QA-MISRA FITS IN YOUR VERIFICATION PROCESS
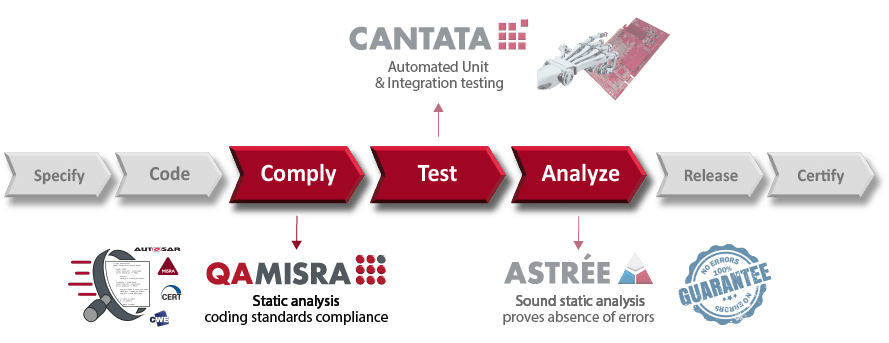
- COMPLY > Use QA-MISRA for fast coding standard compliance at the developer’s desktop first.
- TEST > Use Cantata for automated dynamic execution of the standard compliant software.
- ANALYZE > Use Astrée for proving absence of run-time errors on whole application.
NB: Astrée uses the same configuration as QA-MISRA, so the effort to apply it later to a QA-MISRA project later is low.
Customers can benefit from a bundled solution for both QA-MISRA and Cantata. This means that customers can access a shared concurrent license pool, and the tools can be integrated in the Eclipse-based IDE.
Purchasing QA-MISRA as a bundle with Cantata, or converting an existing Cantata license to a bundle, offers attractive combined prices. For more information, please contact us.
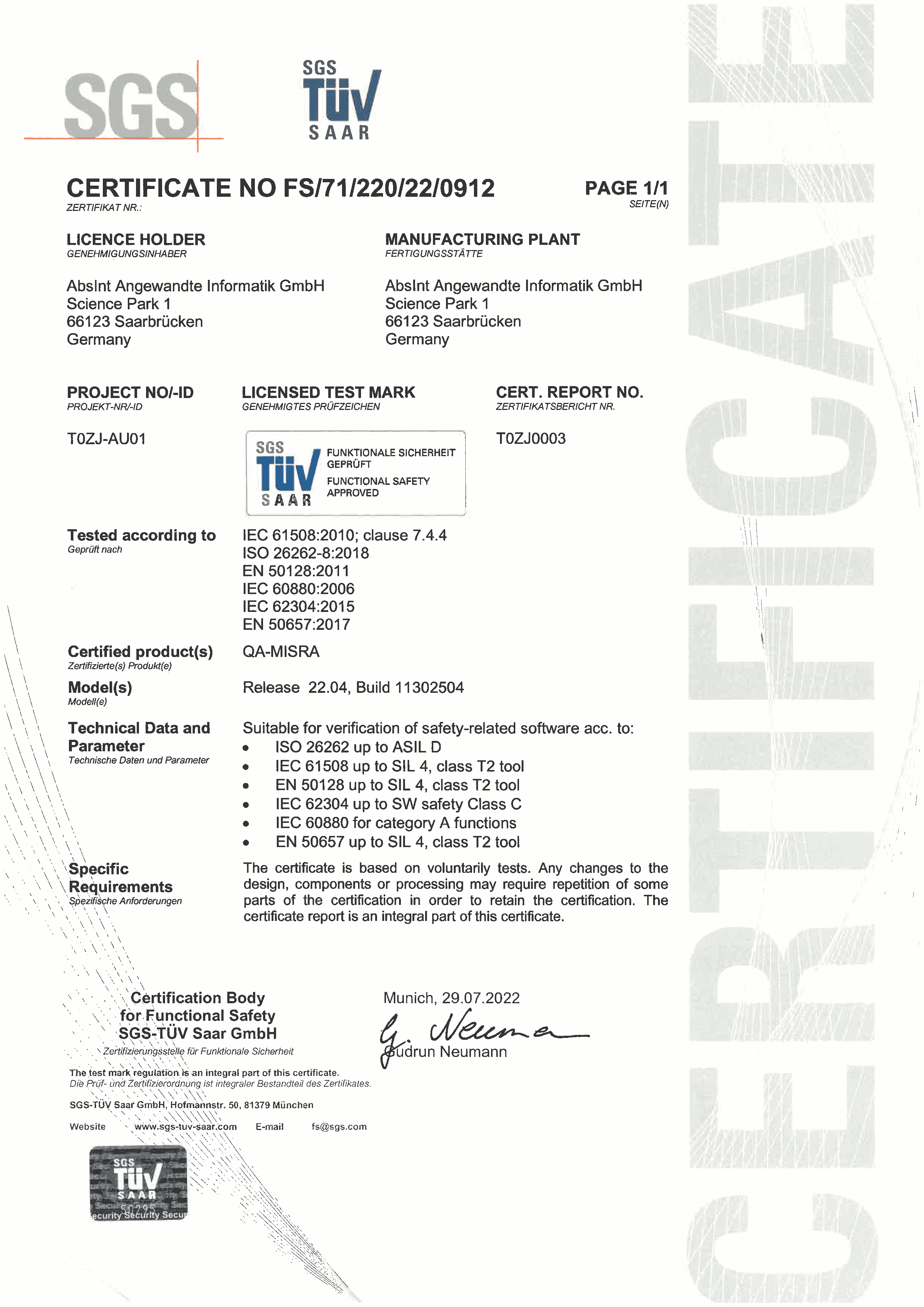
SOFTWARE SAFETY STANDARDS COMPLIANCE
To obtain certification for device software, compliance with international software safety standards is crucial. These standards require evidence of coding standards compliance, and in most cases, verification tools used must be certified/qualified or proven through use.
SGS-TÜV SAAR GmbH has independently certified QA-MISRA for the main software safety standards. Therefore, a QA-MISRA tool certification kit is provided free of charge, which contains everything needed out-of-the-box to help achieve certification for your device software.
CERTIFIED / QUALIFIABLE STANDARDS
International software safety standards require evidence of coding standards compliance to obtain certification for the device software. For further information about each standard please see the links below:
IEC 61508
Functional Safety of Electrical/ Electronic/ Programmable Electronic Safety-related Systems
EN 50128/50657
Railway applications – Communication, signalling and processing systems & Software on board rolling stock
DO-178C
Software Considerations in Airborne Systems and Equipment Certification
OTHER STANDARDS
Automotive – SPICE
ISO/IEC 15504 Information technology — Process assessment
DO-278A
Guidelines for Communication, Navigation, Surveillance and Air Traffic Management (CNS/ATM) Systems Software Integrity Assurance.
ECCS-E-40
Space Engineering: Software
Def Stan 00-55
UK Requirements for Safety Related Software in Defence Equipment
MIL STD 498
US Military-Standard-498 Software Development and Documentation.
NASA 8719.13C
NASA Technical Standard: Software Safety Standard